|
|
Main » 2011 » December » 22
 Certain underground hacking forums are acting as training academies
and tech-support networks for cybercriminals as well as creating a
marketplace for a vast array of cybercrime tools, say researchers. Certain underground hacking forums are acting as training academies
and tech-support networks for cybercriminals as well as creating a
marketplace for a vast array of cybercrime tools, say researchers.
Database security firm Imperva has been keeping close tabs on an
unnamed hacking message board with nearly 220,000 registered members
since 2007. It discovered that the forum is used by hackers of varying
abilities for "training, communications, collaboration, recruitment,
commerce and even social interaction". Chat rooms are filled with
discussions on everything from attack planning to requests for help with
specific campaigns. Newbies can use the forums to find "how-to-hack"
tutorials. Meanwhile the forum's marketplace acts as an underground bazaar for the
sale of either stolen data or attack to
...
Read more »
|
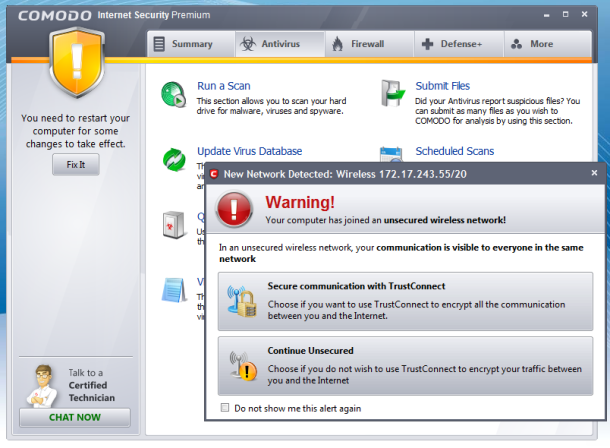
Comodo Internet Security 5.9, which despite following the security
industry naming convention for paid suites is actually the name of
Comodo's free suite, now supports the company's TrustConnect VPN
service. TrustConnect uses 128-bit encryption to provide addition Wi-Fi
protection, although it doesn't anonymize your traffic like Hotspot Shield does.
The TrustConnect integration will automatically detect unsecure Wi-Fi networks and offer to activate the VPN.
 ...
Read more »
...
Read more »
|
V  The international hacker movement "Anonymous" has published an internet video threatening Mexico's Zetas drug cartel with exposure of its allies in the local police and news media this week unless the gang frees a kidnapped member.The YouTube message, which claims to be from Anonymous "Veracruz, Mexico and the world," says it is "tired of the criminal group the Zetas, which is dedicated to kidnapping, stealing and extortion," and threatens to fight back with information instead of weapons. The international hacker movement "Anonymous" has published an internet video threatening Mexico's Zetas drug cartel with exposure of its allies in the local police and news media this week unless the gang frees a kidnapped member.The YouTube message, which claims to be from Anonymous "Veracruz, Mexico and the world," says it is "tired of the criminal group the Zetas, which is dedicated to kidnapping, stealing and extortion," and threatens to fight back with information instead of weapons.
It said it knows of police officers, journalists, taxi drivers and others working with the Zetas.
|
 Back up any files or applications that you want to save. The quickest way to do a back up would be to burn most of your personal files, like photos and documents, with the help of a burn folder.Here you have to follow Total 9 steps are you are ready to run play with MAC OS on a x86 platform. Back up any files or applications that you want to save. The quickest way to do a back up would be to burn most of your personal files, like photos and documents, with the help of a burn folder.Here you have to follow Total 9 steps are you are ready to run play with MAC OS on a x86 platform.
Step 1:- You may need to burn to a DVD if you have lots of things to back up.
Step 2:- Open the Disk Utility application. This program is found in the "Utilities" folder in the application folder on your hard drive.
Step 3:- Select your hard drive in Disk Utility and select the "erase" option. Be sure everything you want to save is backed up first. Shut down the computer when it finishes.
...
Read more »
|
 Malwarebytes’ Anti-Malware is an anti-malware application that can thoroughly remove even the most advanced malware. It includes a number of features, including a built in protection monitor that blocks malicious processes before they even start.Malwarebytes’ Anti-Malware monitors every process and stops malicious processes before they even start. Malwarebytes’ Anti-Malware is an anti-malware application that can thoroughly remove even the most advanced malware. It includes a number of features, including a built in protection monitor that blocks malicious processes before they even start.Malwarebytes’ Anti-Malware monitors every process and stops malicious processes before they even start.
The Realtime Protection Module uses our advanced heuristic scanning technology which monitors your system to keep it safe and secure. In addition, we have implemented a threats center which will allow you to keep up to date with the latest malware threats.
Malwarebytes’ Anti-Malware is considered to be the next step in the detection and removal of malware. We compiled a number of new technologies that are designed to quickly detect, destroy, and prevent malware.
![]() ...
Read more »
...
Read more »
|
 Free Mp3 Player is prone to a remote buffer-overflow vulnerability
because it fails to properly bounds-check user-supplied data before
copying it into an insufficiently sized buffer.An attacker can
exploit this issue to execute arbitrary code in the context of the
affected application. Failed exploit attempts will likely result in
denial-of-service conditions. Free Mp3 Player is prone to a remote buffer-overflow vulnerability
because it fails to properly bounds-check user-supplied data before
copying it into an insufficiently sized buffer.An attacker can
exploit this issue to execute arbitrary code in the context of the
affected application. Failed exploit attempts will likely result in
denial-of-service conditions.
Free Mp3 Player 1.0 is vulnerable; other versions may also be affected.
Exploit Code
#!/usr/bin/perl
# Exploit Title: Free Mp3 Player 1.0 Local Denial of Service
# Date: 19-12-2011
# Author: JaMbA
# Download:
http://www.softpedia.com/get/Multimedia/Audio/Audio-Players/Free-Mp3-Player.shtml
# Version: 1.0
# Tested on: Windows 7
my $file= "Crash.mp3";
my $junk= "\x41
...
Read more »
|
 There are many factors involved in getting your website ranking on
search engines. Below are some key things to take into consideration, and we hope that it will help you to increase traffic on your blog website or forum :) There are many factors involved in getting your website ranking on
search engines. Below are some key things to take into consideration, and we hope that it will help you to increase traffic on your blog website or forum :)
Anchor text
The anchor text of inbound links coming to your website is very
important as search engines use this to determine what your site is
about and what it should rank well for. Your anchor text should be your
keywords that you want your website to rank for. For example, instead
of using your company name or your website URL for inbound links,
consider using keywords as your anchor text.
Use keywords in your title tag and other meta tags
Meta tags still hav
...
Read more »
|
Firefox 9 has been officially released.
The latest update to the popular browser brings several new features and
improvements, the biggest of which is a modification to the JavaScript
engine that provides a big performance boost of up to 30 percent in some
cases.

The latest Firefox uses type inference,
a method of determining and setting the type of a JavaScript variable
at runtime which leads to less overhead and more efficiently used
memory. A more comprehensive explanation as well as some
...
Read more »
|
|
|